Google Wifi and Verizon FiOS
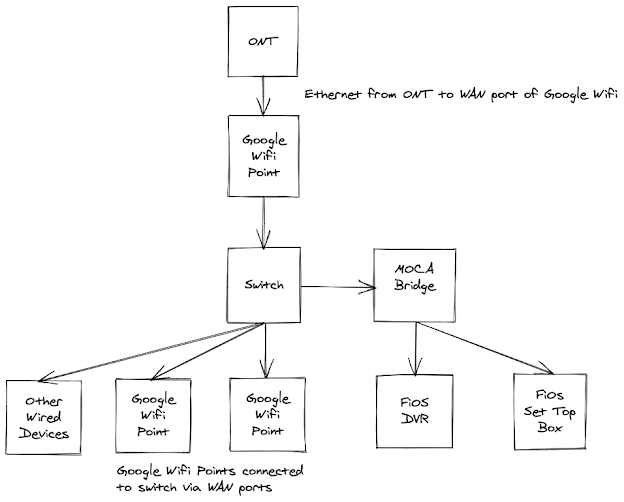
There are a bunch of articles spread around the internet about how to best use Google Wifi and Verizon FiOS together. The concepts are really applicable to any case where you want to replace the Verizon FiOS router with your own, while still retaining full TV functionality (Guide, On-Demand, Remote DVR access, On-Screen Caller ID, etc). My experience drew heavily from several sources, including http://www.dslreports.com/faq/16077 , https://robotpoweredhome.com/google-nest-wifi-verizon-fios/ , and https://www.arhea.net/posts/2020-01-012-fios-own-router.html . My ultimate goal was to completely remove the Verizon FiOS router (in my case, a G1100), while retaining full functionality. The gist of what my setup looks like is below: The components involved here are: FiOS ONT (Optical Network Terminal) Google Wifi Points Any unmanaged 10/100/1000 Ethernet Switch (you decide how many ports you need) MOCA Bridge (Actiontec WCB3000) FiOS TV One DVR (Arris VMS4100) FiOS TV Set Top Boxes (Arris